Whether you grew up with technology or are simply a very hard-working person, you probably think you’re well-versed in dealing with cyberattacks. But most of us have unknowingly been exposed to cybersecurity threats.
Did you know that Australians have already lost more than $186 million to online scams in 2024?
Your personal information could be destroyed. Or you could lose your savings, your identity, your livelihood or more.
The good news is that you can beat scammers at their own game. Follow these 10 simple steps to protect yourself today.
- Check if you’ve already been affected by data theft
Before taking steps to protect yourself from a cyber-attack, check if you’ve already been a victim of one without knowing it. Visit haveibeenpwned.com and change the passwords on any accounts you suspect may have been compromised.
Oh no, my data has been compromised! What do I do? First of all—stay calm. Depending on the type of breach, you may need to take immediate action. If only usernames and passwords for non-critical accounts were stolen, you may not have any major issues. If phone numbers are shared, you should be wary of scams. Be wary of calls or text messages from random numbers (or numbers that seem “trustworthy”).
You should immediately change the passwords for any affected accounts. If you use the same or similar passwords on other accounts, change them as well.
Don’t forget to change the passwords for the following accounts:
- Bank accounts
- Healthcare and government services
- Social media accounts.
Also, when you change your password, say “Yes” when you’re asked to sign out of that account on all your other devices.
2. Test the strength of your password
Test the strength of your password at howsecureismypassword.net (as an added security measure, you can test the strength of your original password). When choosing a password, keep in mind that the longer it is, the stronger it will be. A strong password is at least 14 characters long and difficult to guess.
Alternatively, use a passphrase to strengthen your cybersecurity measures.
Using a phrase (passphrase) is a great way to create a long password that you will never forget.
Compared to “D3nt@o9e,” passwords like “RabbitCheesePencil#3Outlook” is more memorable and powerful. Just change the “Outlook” part depending on what you are logging in to.
3. Avoid these passwords
The following passwords are considered to be the most common and easy to crack. So, if you have any of these passwords or similar variants, you should seriously consider changing them immediately.
- 123456 (or numbers in chronological order)
- 987654321
- 123123 QWERTY
- 111111 44 44 Password
4. Use a password manager
Tired of remembering all your passwords or changing them every time you log in? Choose a password manager that can help you securely store and create passwords. This is very convenient because once you set it up, you only need to remember one master password.
A password manager allows you to create unique, complex passwords for your work and personal accounts. Your PM will also store them securely in their system and enter them when you log in to websites.

VU Cyber has partnered with Dashlane to offer VU students a free password manager.
Dashlane stores your passwords and keeps them up to date across your phone, computer, tablet, and other devices (including personal devices).
5. Use multi-factor authentication
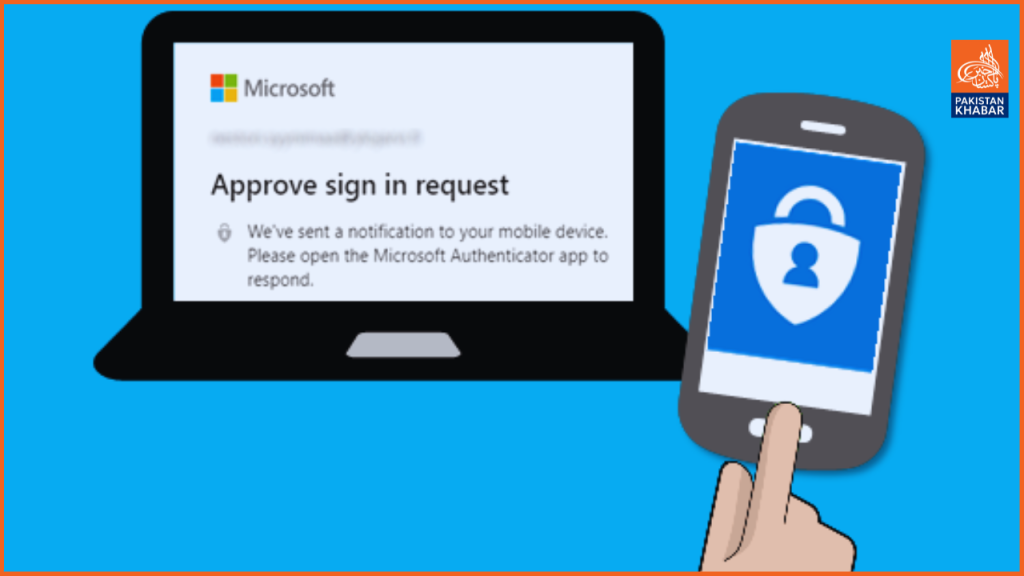
Use multi-factor authentication for an additional level of protection. Also known as two-factor authentication, MFA, and 2FA, this authentication adds an extra layer of security to websites, helping them verify that you are who you say you are.
You may be asked to prove your identity in a variety of ways, but your mobile phone is usually the key. When you log into your banking software, you might be asked to enter your PIN. Or when accessing your work email, you might be asked to use an MFA app like Microsoft Authenticator.
6. Don’t trust anyone (email, phone, or text message)
This may sound a bit extreme, but always be wary of scam emails and manipulated websites (spam and phishing). Interacting with these could put your information at risk and download a virus.
Caution:
- Don’t open emails from unknown email addresses.
- Trash unexpected email attachments.
- Avoid risky clicks. Type the address into your browser instead.
The sophistication of scammers and hackers is increasing. Protect yourself from cyberattacks by being wary of text messages you receive, especially those that ask you to enter your credit card information.
For example, if your bank calls you and leaves a message and number, be sure to verify the number online before calling back. And whatever you do, never give out personal information over the phone or email unless you’re sure it’s safe. You don’t want to be a victim of “social engineering,” where people are tricked into disclosing sensitive personal information by people who appear reputable but are actually bad people.
If you are contacted by phone by someone requesting personal information, ask for his name and phone number and offer to call him back. Just because he may have some of your information does not mean he is who he says he is.
7. Protect your device
If your mobile device is not protected, if it is lost or stolen, it can be used to access your information and money or to steal your personal information and irreplaceable data such as photos and messages.
Protect your device by:
- Install antivirus software
- Set a password, gesture or fingerprint that must be entered to unlock it
- Set your device to require a password before installing applications
- Hide Bluetooth when not in use and disable automatic connection to networks for devices that support it; enable the lock and/or wipe feature remotely.
8. Update your software
Regularly update the software systems on your devices (phones, tablets, laptops). In fact, don’t forget to turn on automatic updates so that the work happens in the background.
Network defenders patch system vulnerabilities and make them inaccessible to malicious attackers. We must do our part by updating our software with the latest fixes. And it’s not just hardware that needs to be updated. Make sure your applications are up to date and that you’re browsing the Internet with the latest version of your browser. And of course, antivirus software! It can protect you to a great extent from cyberattacks.
9. Use a secure web browser
Stick to websites that use the green padlock and “HTTPS.”Only when you see this padlock enter any sensitive personal information, such as TFN or credit card, when buying something online.

If a website has an “invalid certificate,” this may indicate that it is not trustworthy and should be avoided. Pay close attention to website URLs too. Malicious websites often use different spellings or different domains (e.g., .org instead of .com) to deceive web users.
Also, only download files from trusted websites. Otherwise, the file may contain a virus (ransomware) designed to spy on you or blackmail your computer.
10. Report anything suspicious to your IT department
If you receive a suspicious email or file at work or school, report it to your company’s IT department.
After all, they are professionals and can do some research to see if they received a phishing link or if the file or email in question is genuine. Now you should be a lot more Internet savvy and know what to look out for when surfing the web.



